Aegis Ecosystem
Autonomous Robot

Enhanced secure delivery system features a secure automated storage compartment, anti-tampering system and 360 degree surveillance
Companion Application
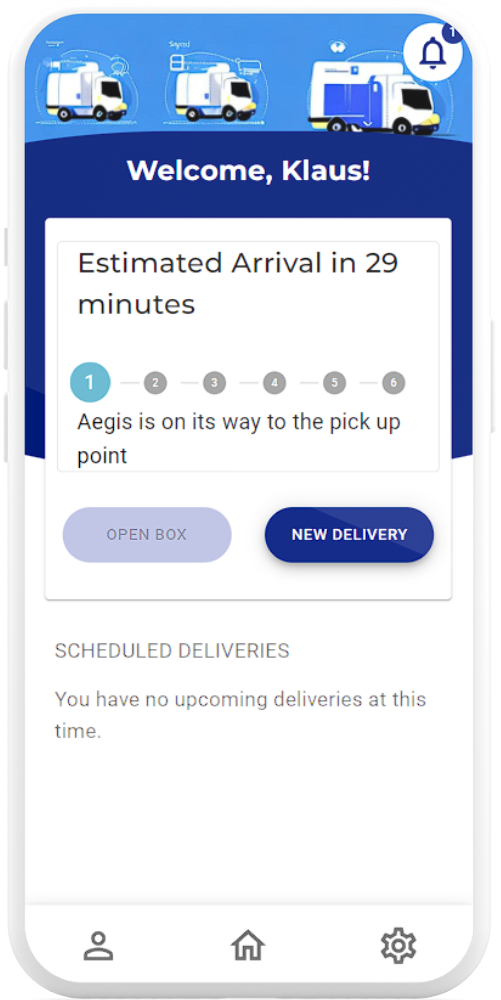
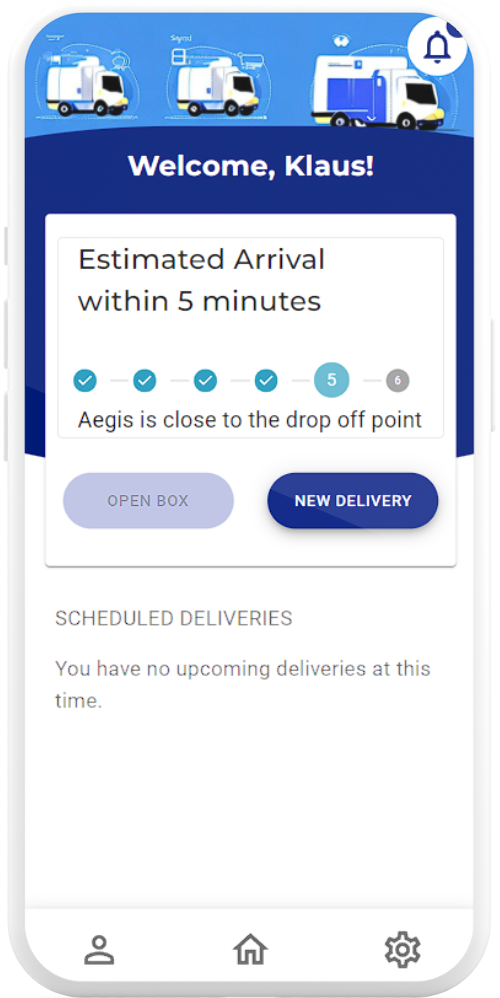
Schedule new deliveries and track ongoing ones with ease via the live tracking feature on the Aegis mobile application
PRODUCT VIDEO
Aegis 360 View
User Journey
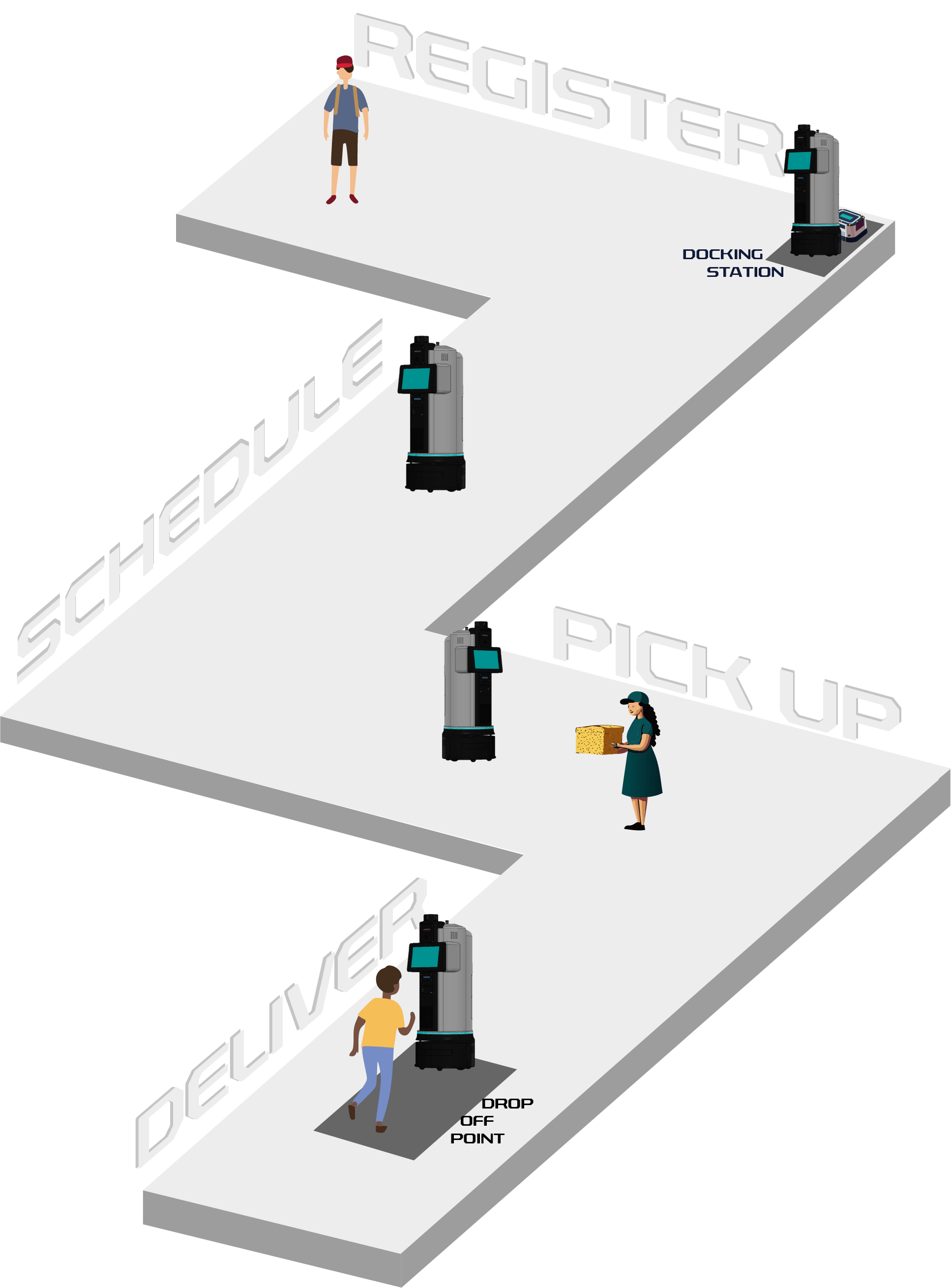
Stage 1: Register
Register for an Aegis account with the system administrator by providing your name, email address, phone number and photos, which will be used for facial recognition

Stage 2: Schedule
Schedule a delivery using the Aegis mobile application
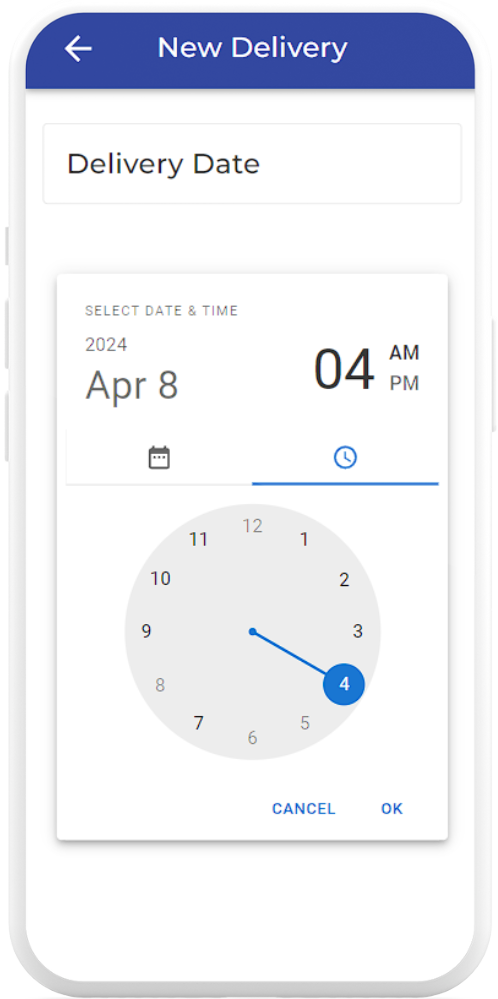
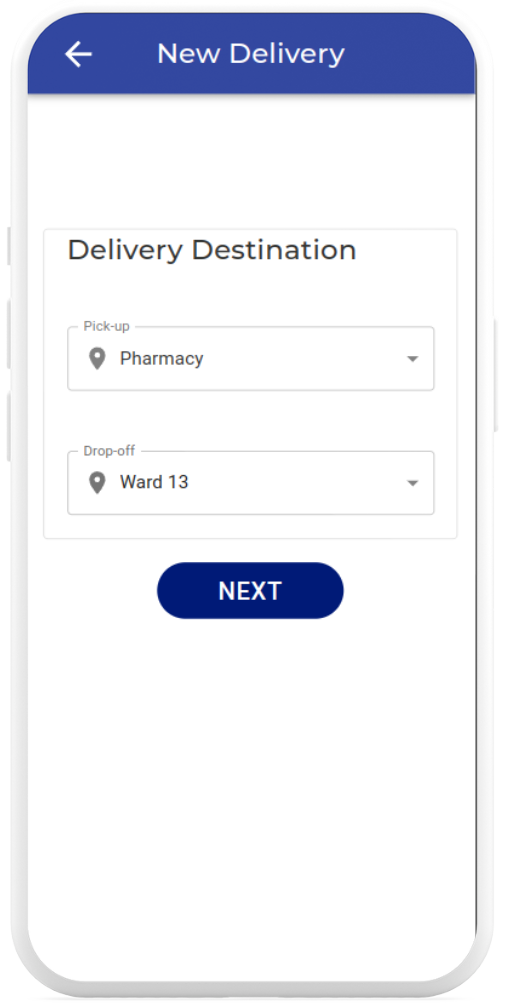
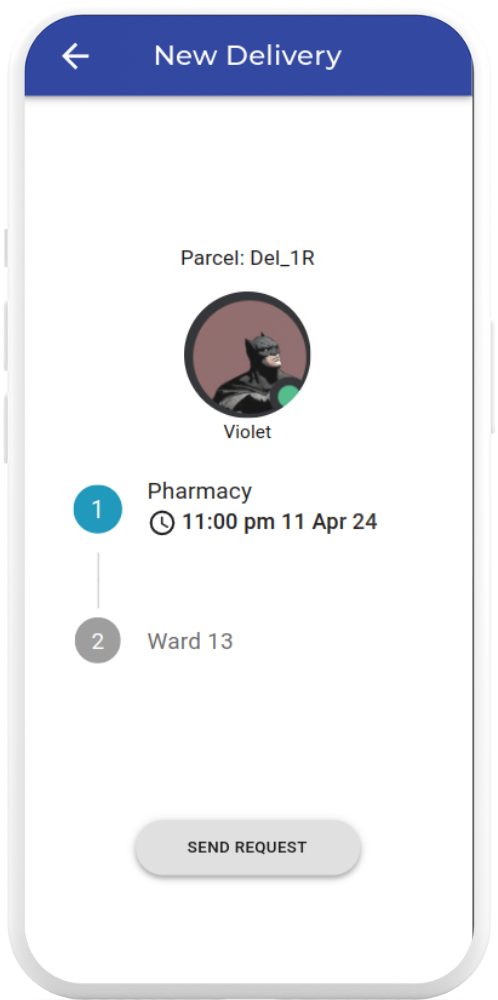
Stage 3: Pick Up
At the scheduled delivery timeslot, Aegis travels to the pick up point, where you can place the parcel into the secure compartment after completing facial recognition and time based one time password (TOTP)
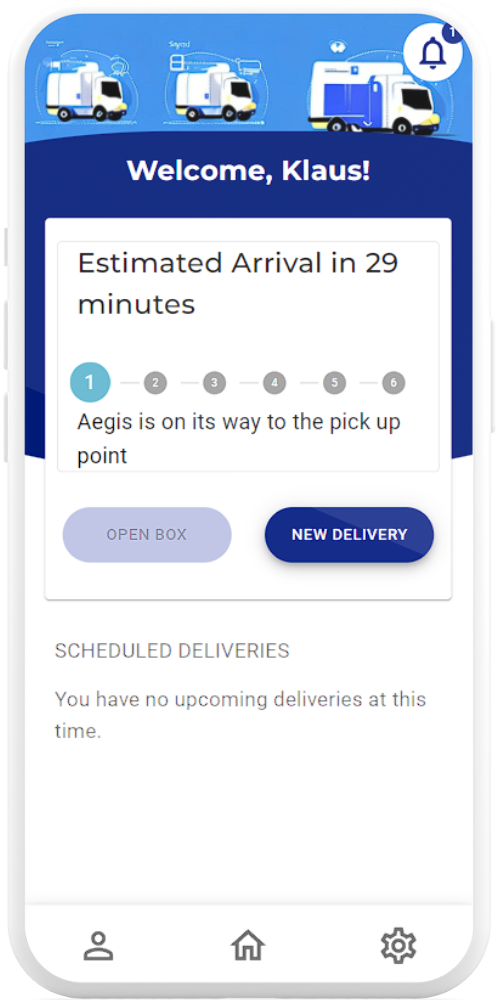
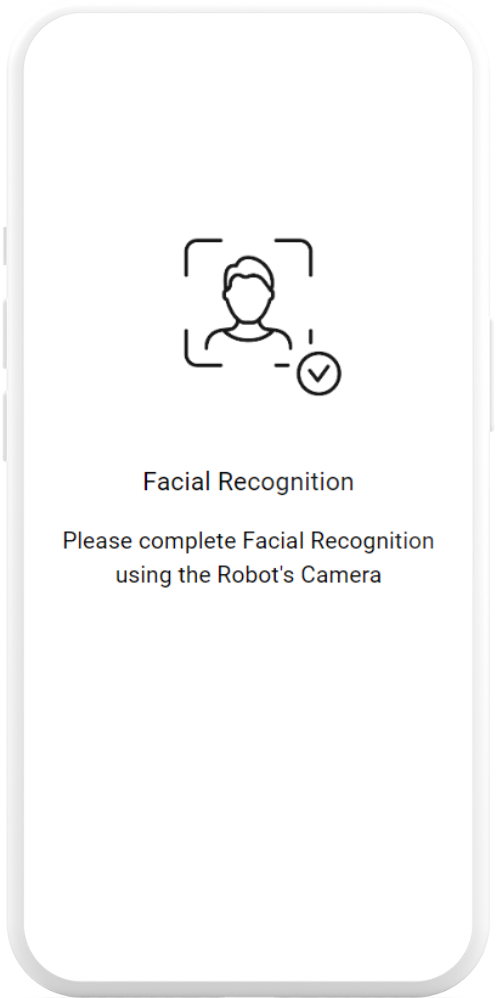
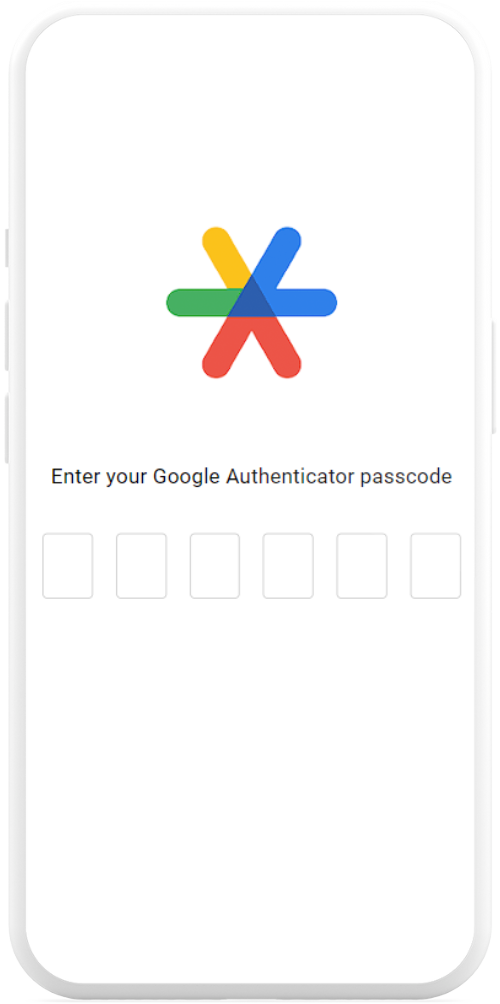
Stage 4: Deliver
The receiver picks up the parcel from the secure compartment after completing facial recognition and TOTP
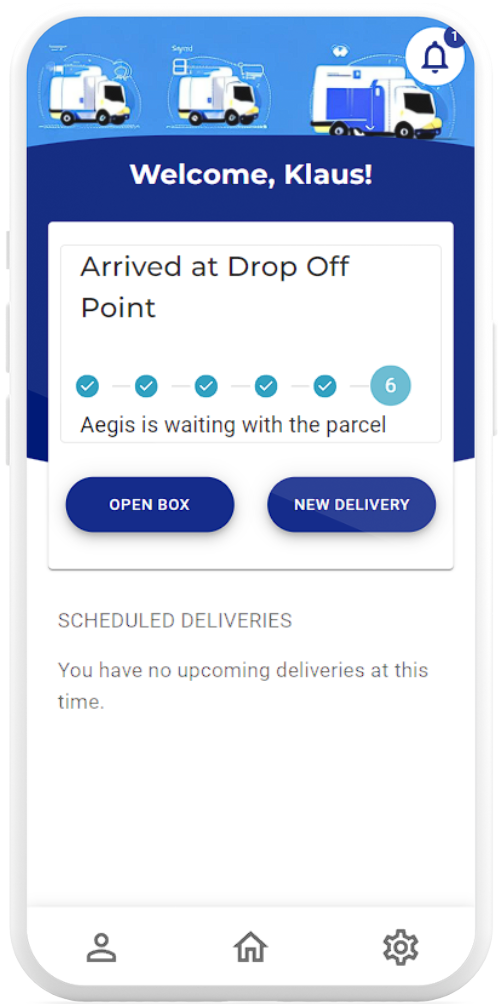
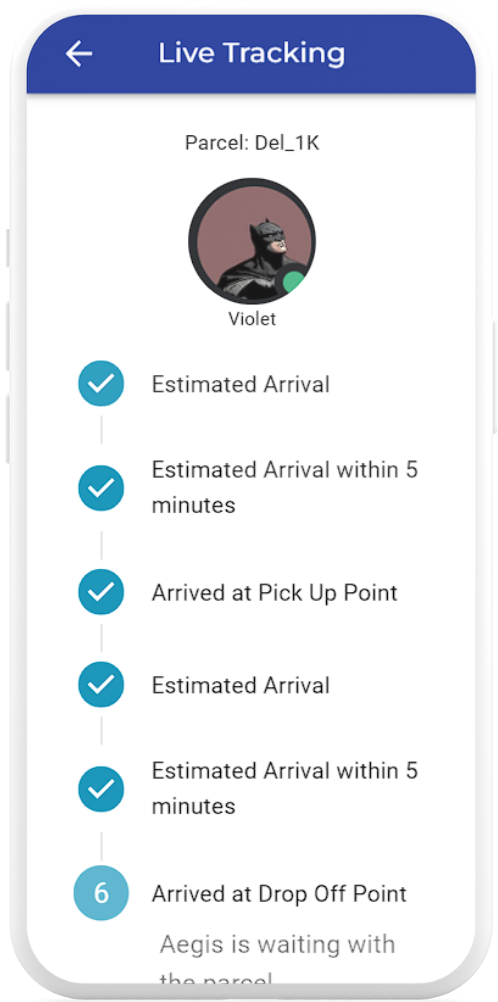
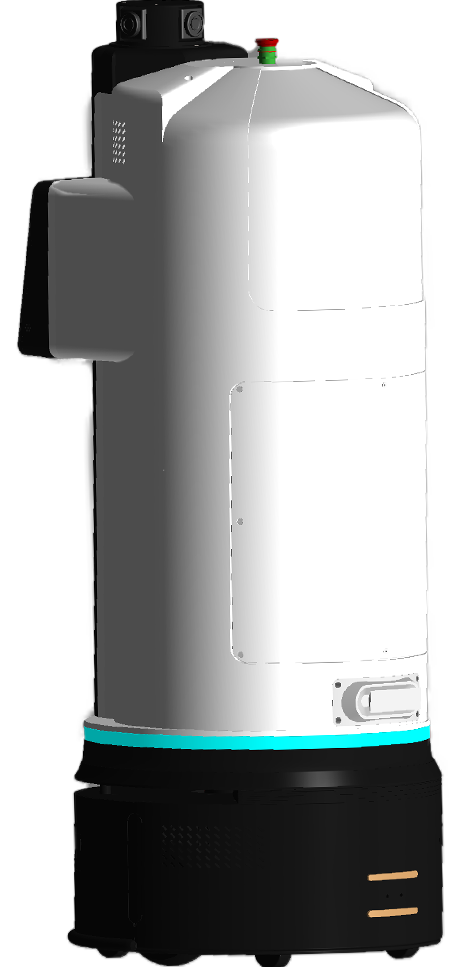
Electro-Mechanical Features
Sleek Design
- Sleek, seamless design
- No obvious points of entry for easy tampering
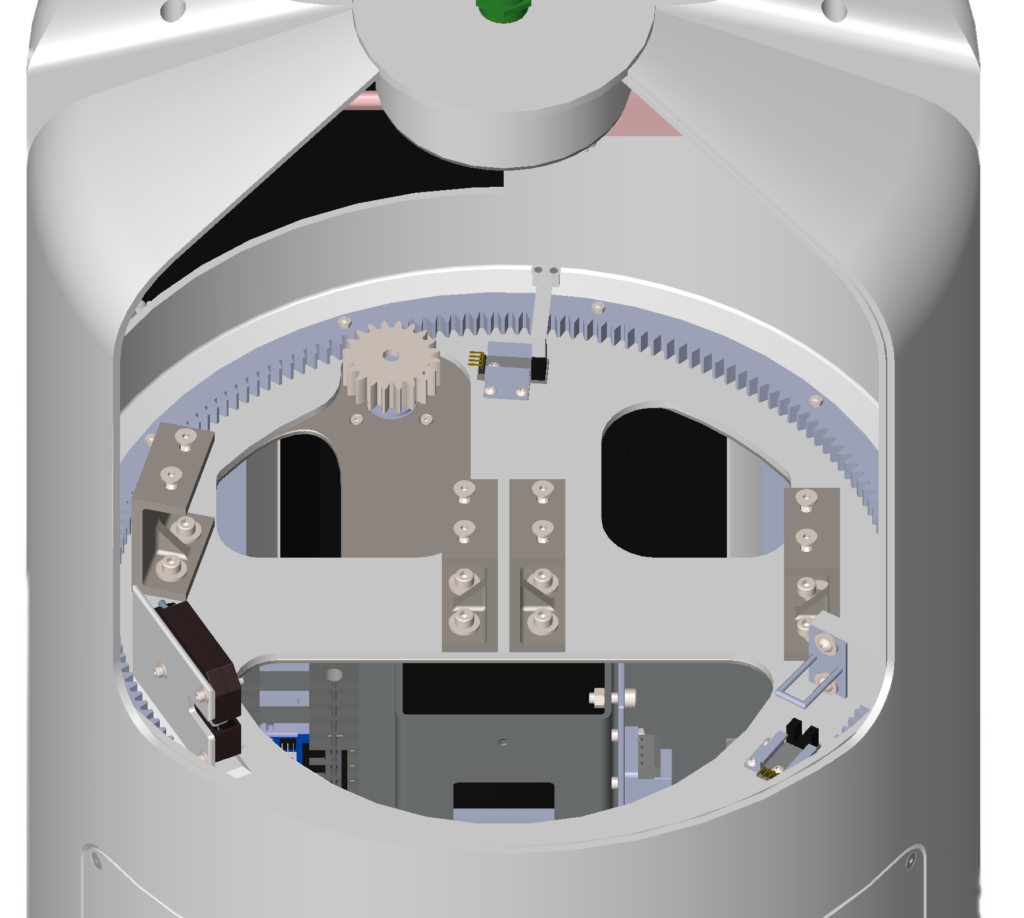
Anti-Tampering System
- Mechanical Lock
- Metal case prevents electromagnetic tampering
- Only disengages upon successful user authentication
- System remains locked in case of electrical failure
- Alarm system to detect tampering
- Sounds when the compartment has been pried open
- Alerts security about a security breach
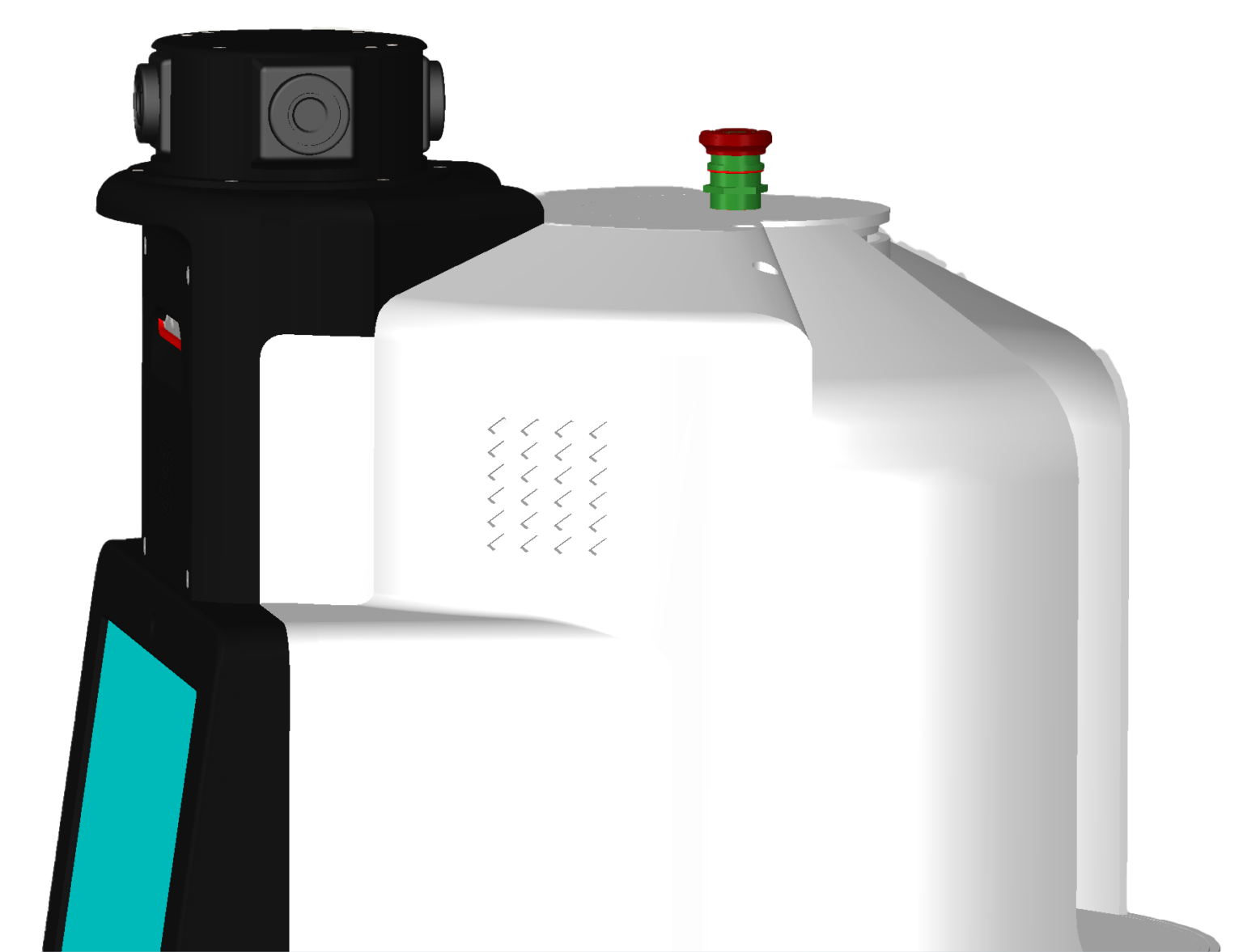
360 Degree Surveillance
- 4 IP cameras provide 24/7 video surveillance
- Surveillance videos are stored for a day and can be retrieved for future investigations
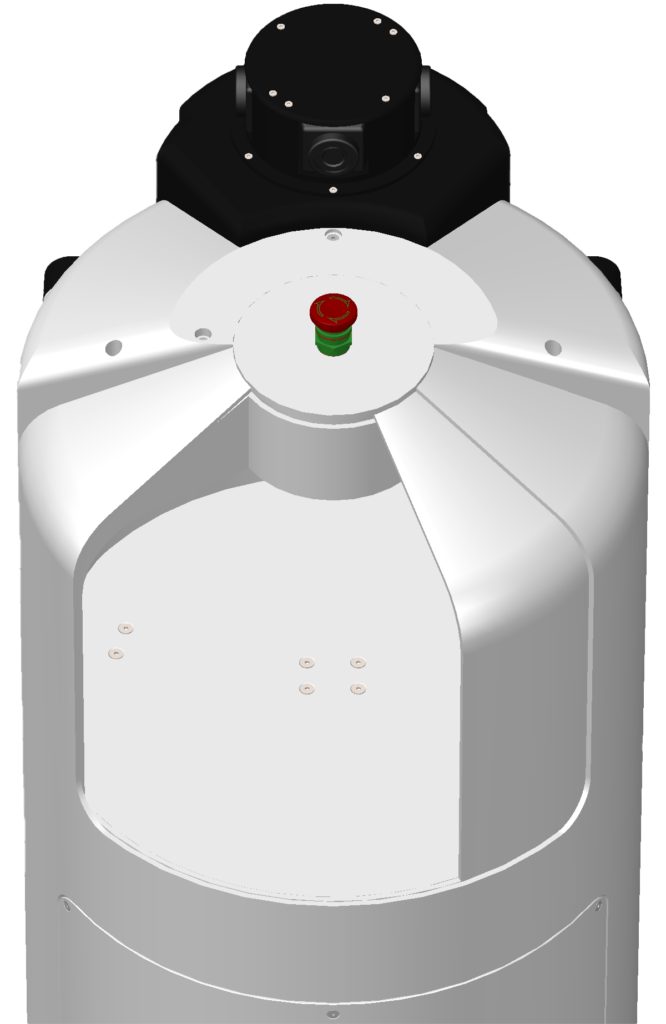
Secure Storage Compartment
- Panel automatically opens for user to access their parcels
- Only accessible after successful user authentication
- Fully automated system: integrated with the Aegis mobile application to improve user experience
Digital Security Features
Multi-Factor Authentication
- TOTP using Google Authenticator
- Facial Recognition trained using K-Nearest Neighbours model


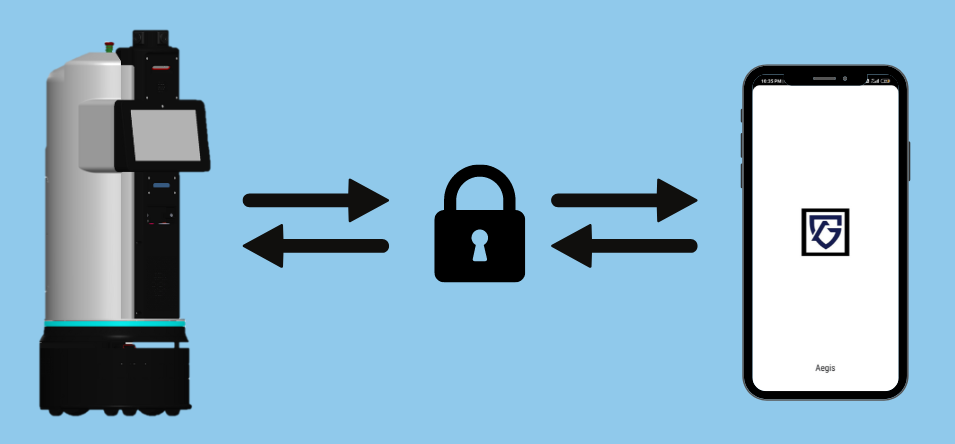
Secure Data Transmission
- Elliptic Curve Integrated Encryption Scheme (ECIES) using AES and SHA256 hashing algorithms on secp256k1 curve for encryption and message authentication ensure that data transmitted between the mobile application, robot and database are encrypted and secure
Database Encryption
- Hashing passwords to get keys (DEK and KEK) using Argon2ID
- Keys are then used to create an envelope encryption scheme

Account Security
Log In/Change Password
- Password Selection
- Minimum length 8, blacklist check to prevent trivial bruteforce and rainbow table attacks
Log In and Change Password
- Double-submit anti-CSRF token to prevent request forgery and anti-CSRF token forgery
- JWT and RT Theft Detection
Revocation of detected stolen tokens
TOTP
256-bit pseudo-random seed unique to user
- Password Selection
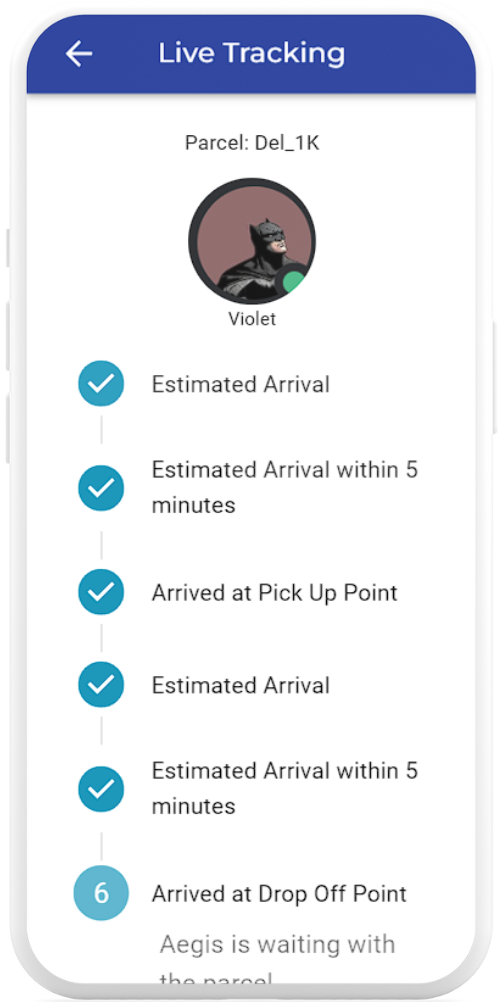
Live Tracking
- Track deliveries through their various stages through the mobile application’s live tracking feature
- Receive live push notifications when the Aegis robot is nearby
Threat Modelling
Industry standard threat modelling frameworks were used to identify and fix possible vulnerabilities in the software security
Open Web Application Security Project (OWASP) Threat Dragon Threat Modelling Tool
Deciduous Attack Tree Modelling Tool
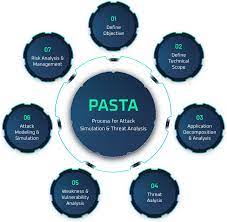
VerSprite Process of Attack Simulation and Threat Analysis (PASTA) Modelling Methodology


Key Benefits
Contactless Delivery
Reduce human-to-human interactions during the delivery process
Reduce Manpower
Reduce the amount of personnel needed to transport high-value goods
Increased Efficiency

Redistribute manpower to optimise efficiency
Poster
Please scan the QR code to view our poster

In Collaboration With:

Acknowledgements:
The team would like to thank our capstone mentor, Dr. Teo Tee Hui, and our CWR mentor, Dr. Susan Wong for their expertise and patient guidance throughout the entirety of the project duration. Additionally, the team would like to extend our gratitude to our industry mentor, Mr. Michael Sayre, and the engineers at KABAM for their expertise, guidance and resources provided.










