Our Video
Cybersecurity
With cyber threats on the rise, organizations face growing risks to their systems and data. To help companies better prepare and respond, we are collaborating with one of Asia’s largest cybersecurity firms. This partnership strengthens cyber resilience through expert guidance and advanced threat protection. Together, we aim to ensure businesses stay ahead of emerging cyber risks.
Table Top Exercises (TTX)
Tabletop exercises are discussion-based simulations designed to help organizations test and improve their incident response plans. Participants, including key stakeholders and decision-makers, engage in structured scenarios that simulate cybersecurity incidents, natural disasters, or business disruptions.
These exercises help teams assess their readiness, identify gaps in their response strategies, and enhance coordination in a controlled, low-risk environment. The goal is to improve decision-making, refine protocols, and ensure a swift, effective response to real-world crises.
Problem Statement
How might we automate this processes to reduce labor and man-hours while maintaining or improving accuracy and effectiveness?
Current Stages and Painpoints
Description
Aligns project objectives and scope with the client
Collects detailed client requirements and context
Helps the team understand the client’s environment to build realistic scenarios
Pain Points
Undocumented requirements
Incomplete or inconsistent document formats

Description
Develops exercise materials (scenarios, injects, artefacts) manually using PowerPoint and Excel
Customised content tailored to each participant group
Pain Points
Manual creation is time-consuming and detail-intensive
Requires creativity and customization for each group

Description
Exercise conducted over 1–2 days, either physically or virtually
Materials are shared in phases using an automated email scheduler
Pain Points
Uploading artefacts to the scheduler is inefficient and time-consuming
Frequent scheduler crashes cause last-minute troubleshooting and stress
Description
Participant actions are observed and evaluated using the NIST Cybersecurity Framework (CSF)
Observations are mapped to CSF categories, scored using a rubric, and compiled into a report with recommendations
Pain Points
Mapping observations to CSF categories is tedious and time-consuming
Observations are handwritten, making digitisation inefficient
Observers must multitask between tracking, recording, and engaging participants
(This stage is not implemented as part of the solution)
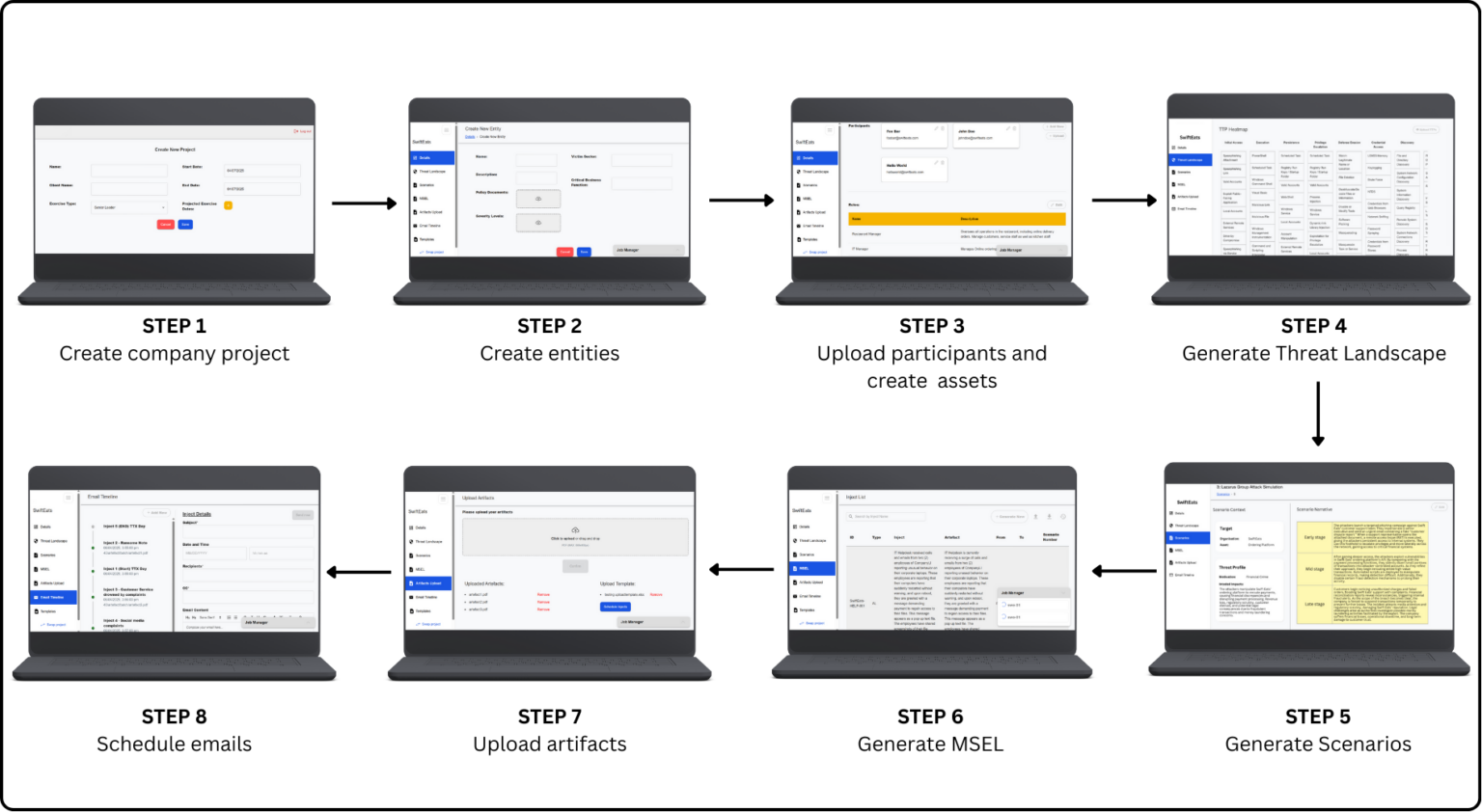
User Flow
Key Features
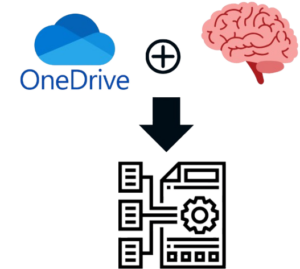
Data Management
Current Issues
Files scattered across multiple ShareDrive folders.
Inconsistent file formats.
Difficult and time-consuming to manage.
Improvements
Centralized storage in one platform.
Consistent file structure and format.
Smooth and efficient file access.
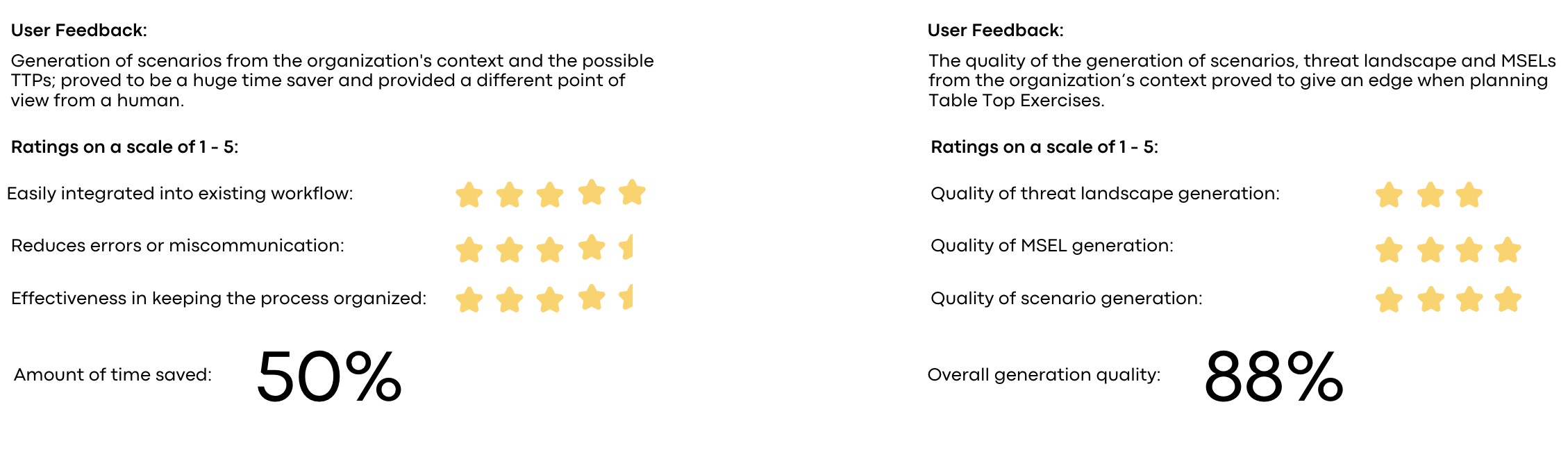
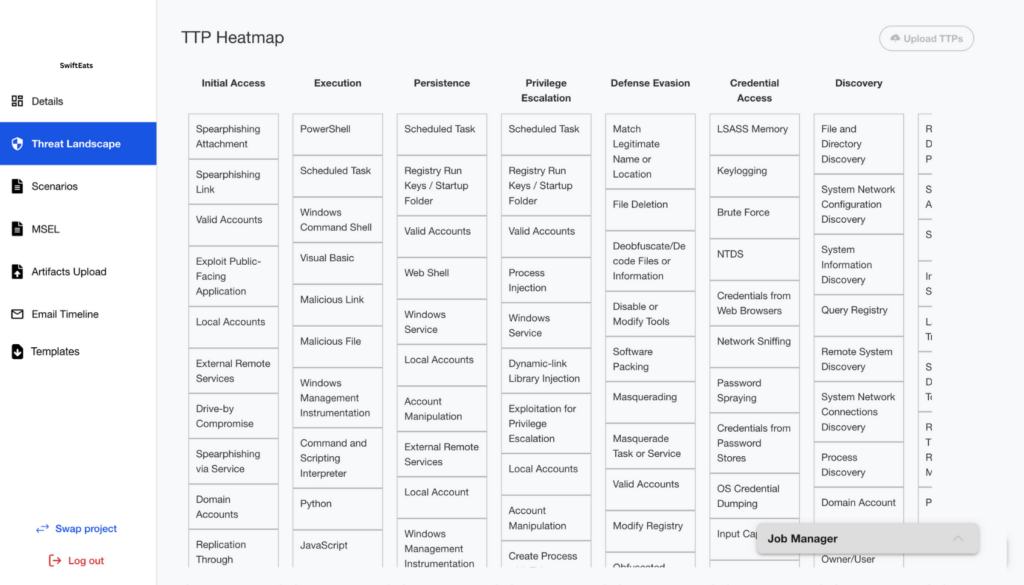
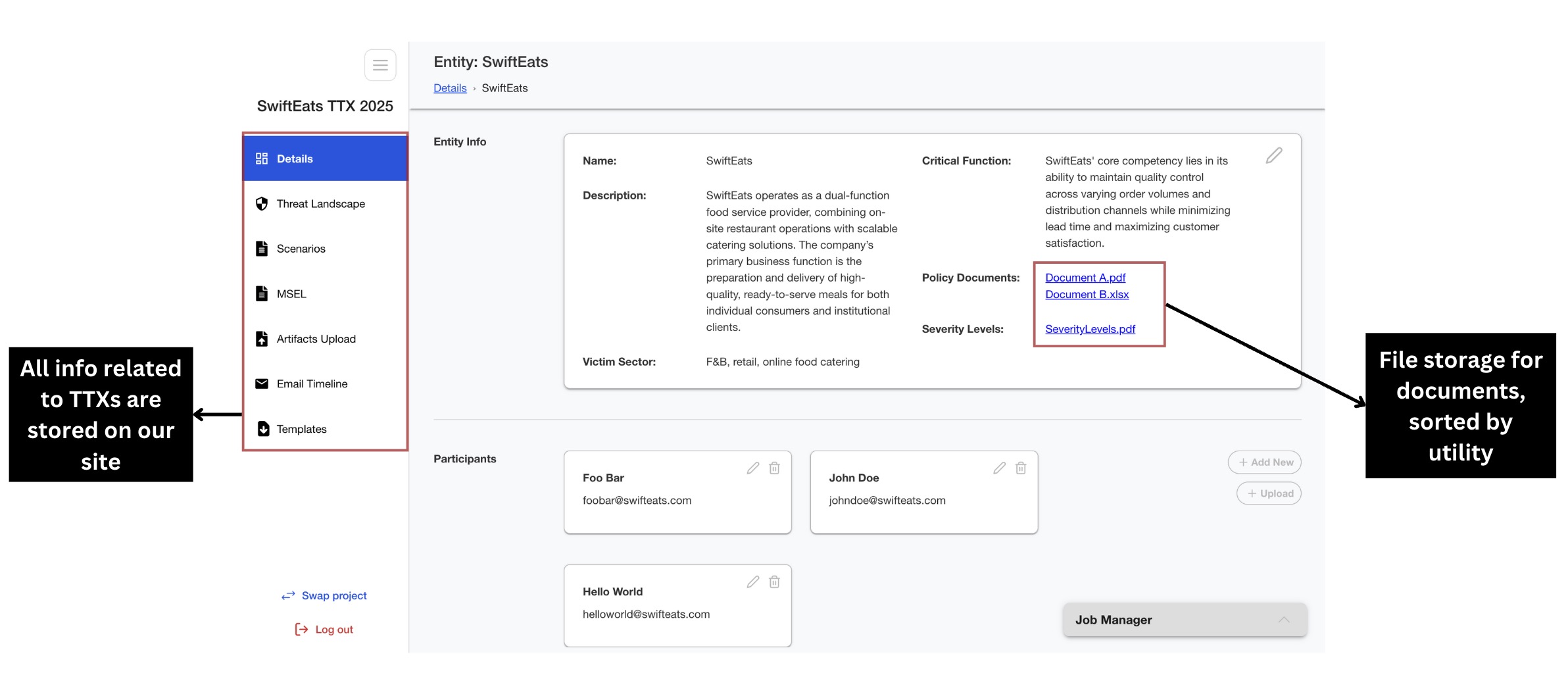
Threat Landscape
Identifies relevant threat actors based on the organization’s context and maps their behaviors using the MITRE ATT&CK framework. This supports targeted threat modeling and proactive risk mitigation by aligning threat intelligence with likely tactics, techniques, and procedures.
Current Issues
Handled using Excel right now.
Manually categorise threat actors and their capabilities, intent and opporunities.
Difficult and time-consuming to manage.
Improvements
Upload JSON file into software.
AI in software will analyse threat actors and categorise them.
Saves time and energy.
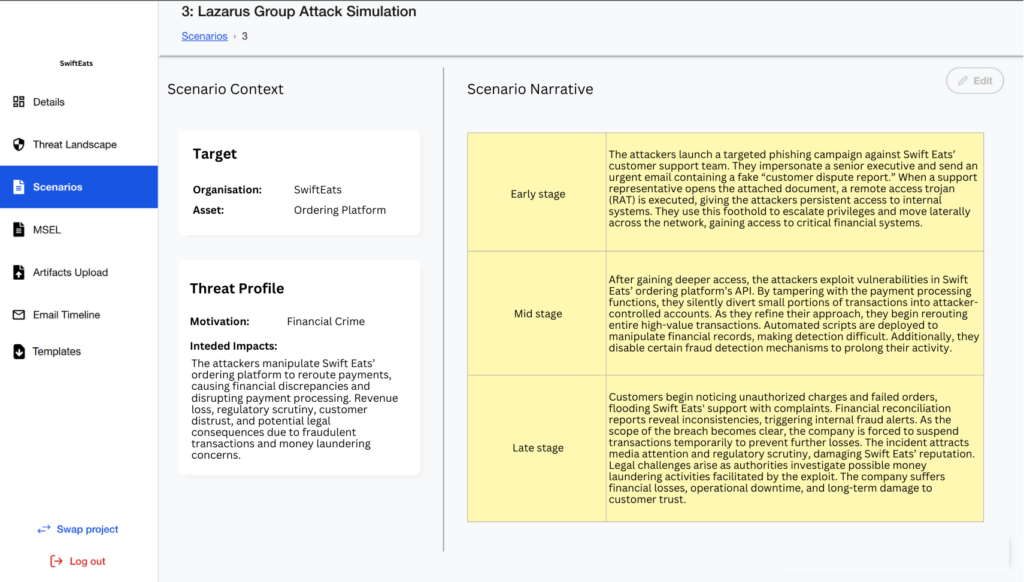
Generate Scenarios
Current Issues
Manually create scenarios on multiple power point slides.
Time-consuming because requires attention to detail and creativity.
Improvements
Generates tailored and context-rich content from user prompts.
Refines scenarios iteratively based on feedback.
- Delivers engaging, human-readable outputs for users.
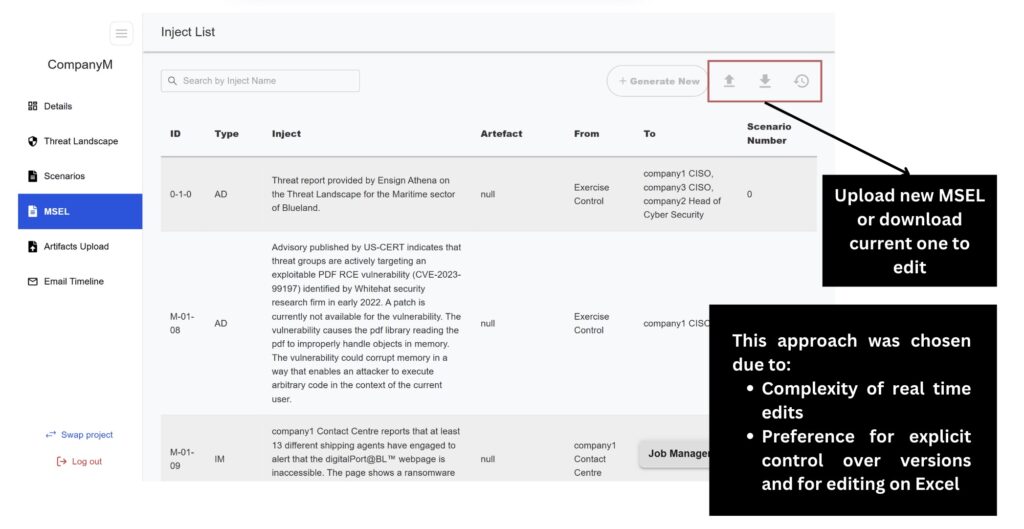
MSEL Generation and Version Control
Each inject is crafted to simulate specific incidents or decision points, guiding participants through the scenario. All of the injects form a sequence of events which forms the Master Scenario Event List (MSEL)
Current Issues
Injects and MSEL are manually created, requiring significant effort and brainpower.
No version control — multiple versions are manually stored and tracked.
Difficult to manage and update injects across different scenarios.
Improvements
Automatically generates injects in chronological order for realistic exercises.
Supports dynamic and tailored inject creation using scenario inputs and context.
Built-in version control ensures easy tracking and management of changes.
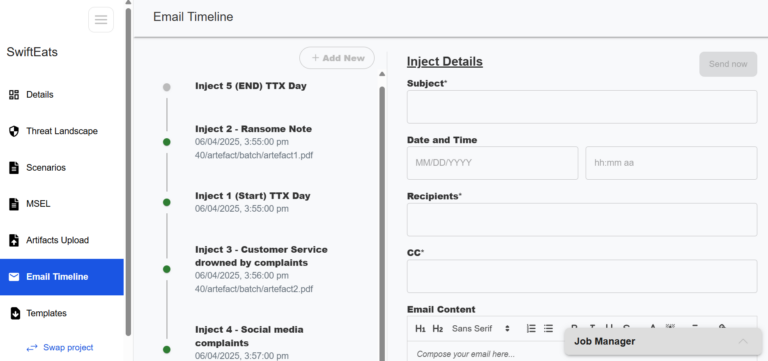
Email Scheduler
Current Issues
Users had to toggle between multiple screens to view schedules and email content.
Attachments were managed on a separate tab and selected from a dropdown list.
No error handling for artefact uploads, leading to confusion when issues occurred.
Improvements
Intuitive and streamlined UI for easier scheduling and email management.
Introduced email lists for faster and more efficient recipient selection.
Seamless attachment uploads directly within the email creation page, with helpful error messages for artefact issues.
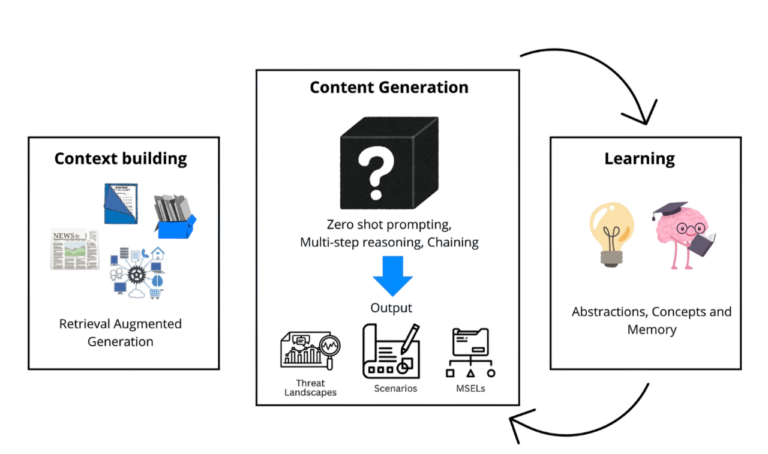
Generation Workflow
Evaluation